Employees have access to all kinds of digital distractions every minute of the day. So, businesses have to make a decision what is acceptable for Internet use when employees are on the clock. This decision can be hard. There are many who think of privacy issues, not wanting to deter human interaction, or who even have a “my managers watch over their employees so I leave it to them” thought. The only real problem is . . . it’s your business that will suffer if Internet-usage privileges are abused on a regular basis. Bandwidth slowdowns and productivity loss, not to mention increased malware risk, can have a substantial impact on your business. No matter which decision you make for your business, you still need to know what is happening to keep your company, your data, and your employees secure and productive.
You need visibility. If you keep up with our Wavecrest posts, we tend to emphasize this point a lot. Why? Because it is a crucial business tool for today’s digital workplace! You have to know what is happening in your business and on your network so you can make informed business decisions. In this particular case, you need visibility into employees’ time spent online.
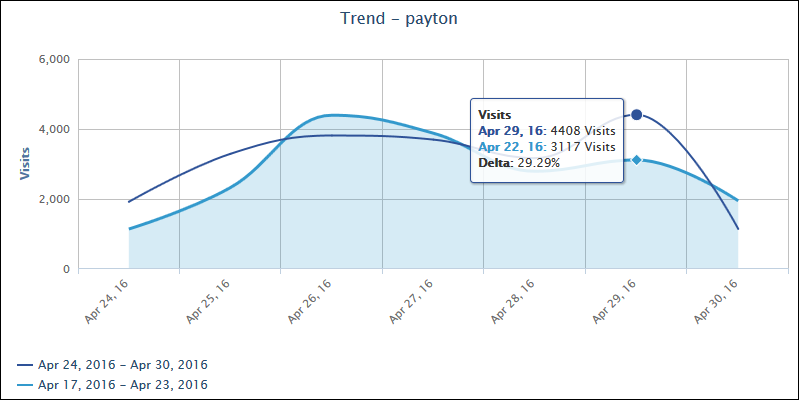
Wavecrest Computing’s Time Online feature provides the time that a user spends on the Internet in a useful and informative format with easy-to-interpret charts. Find out which users spend the most time online, spot spikes, and analyze usage for productivity issues or potential bandwidth hogs. Each business is unique and your Internet-use policy should fit your specific business needs. Find the visibility necessary to keep productivity high and mission-critical operations running smoothly, with Cyfin and CyBlock solutions from Wavecrest Computing.
About Wavecrest Computing
Celebrating 20 years in business, Wavecrest Computing, headquartered in historic downtown Melbourne, FL, has provided commercial business and government clients with reliable, accurate Web-use management and Cloud Access Security Broker products since 1996. Managed Service Providers, IT specialists, HR professionals, and business managers trust Wavecrest’s Cyfin and CyBlock products to manage employee Internet usage — managing cloud services, reducing liability risks, improving productivity, saving bandwidth, and controlling costs. Wavecrest has clients worldwide, including General Electric, Lockheed Martin, Florida Department of Health, Siemens, Department of Homeland Security, and a growing list of global enterprises and government agencies. We are a proud long-term GSA contract holder. For more information on the company, products, and partners, visit https://www.wavecrest.net.