We are pleased to announce the release of three new audit reports in the new versions of Cyfin and CyBlock, which can provide management with detailed Web-use data on specific employees. These audit reports could be of interest to corporate IT forensic personnel, law enforcement agencies, anyone in the legal community, and forensic criminal investigators. They are capable of processing large amounts of log file data and support several types of log file formats such as Blue Coat and IronPort. The new reports are as follows:
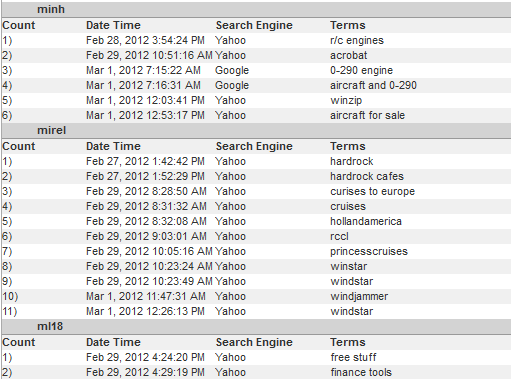
- Search Terms Audit Detail – The report shows search terms that users entered on popular search engine sites such as Google. It includes an option to show “prefetched” search results that were performed as the user was typing. These results are referred to as keystroke searches. This report can be used as a tool to aid in forensic investigations. It also indicates the number of search terms entered and can give the details of a user’s keystrokes.
- Denied Detail – The report shows the specific URLs to which users were denied access. The data is broken out by user. Each Web page attempt is displayed with its corresponding category. Denied attempts for a Web page can signify that the user may not be authorized to receive the page, the page may not have been found by the Web server, or the page may have been blocked for access. If you have Web filtering enabled, this report can verify that it is working and is a very useful supplementary tool for individual user audits.
- Legal Liability Detail – The report shows the specific URLs of Legal Liability Web activity by user, that is, visits to only the Anonymous/Public Proxy, Cults, Drugs, Gambling, Hate and Crime, Malware, and Pornography categories that pose a legal liability risk. By reporting on only these categories, smaller, more focused reports are available to facilitate analyses, investigations, and audits related to legal liability issues.
To see the full release notes for your product, visit the Support Forum. You can download the latest release by going to the Administration – Product Update screen in your Cyfin or CyBlock product.
