Since 1996, Wavecrest has been creating solutions that help customers implement and enforce their Internet Usage policies. As the Internet landscape changes, some websites that were once categorized as unproductive are not so clear these days, causing current Acceptable Use Policies (AUP) to impede necessary productivity as organizations struggle to keep up with the ever-changing Internet. As part of Wavecrest’s mission to constantly improve, the coaching feature has recently been added to CyBlock Proxy v6.7 and CyBlock ISA / TMG v6.7 to alleviate this growing concern.
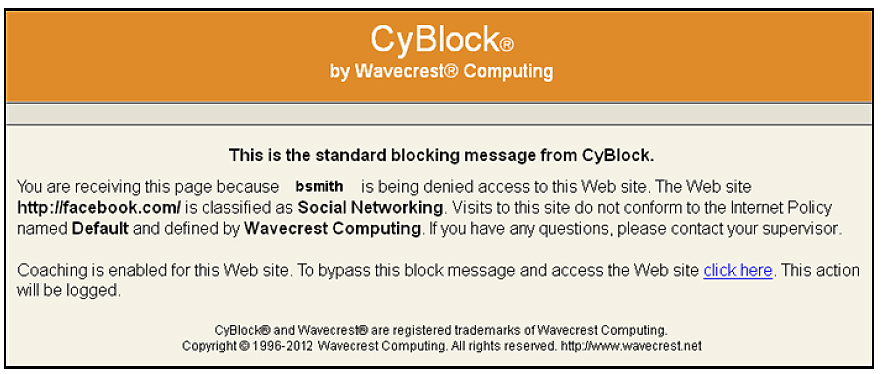
Customize this Message to Reflect Company AUP
This optional-use, customer-configurable, policy support feature allows authenticated / authorized users to override CyBlock’s blocking function while allowing them to proceed to the site they have requested. Coaching can be enabled on categories that have been set to “block”, and policies are customizable based on time of day, user name or group. The coaching feature provides customers with more flexibility and control while continuing to support their company policies through custom block messages.
For more information using CyBlock’s coaching function and creating your own custom blocking message, check out our easy-to-follow instructions on our latest Tech Tip: Create a Custom Blocking Message While Coaching.