Wavecrest Computing celebrates 16 years of loyal customers who have helped the company become a strong, thriving, and innovative business. “What makes Wavecrest stand out from competitors is the on-going commitment to customers and customer service. When customers call, they talk to a real person and they receive personalized attention every time.” Read more about Wavecrest Computing’s products and history: https://www.globenewswire.com/news-release/2013/10/07/578419/10051153/en/Wavecrest-Computing-Celebrates-16-Years-of-Business.html
Category Archives: Wave News
Cyfin Release 8.8.3 and CyBlock Release 6.8.3 Now Available
We are pleased to announce the release of three new audit reports in the new versions of Cyfin and CyBlock, which can provide management with detailed Web-use data on specific employees. These audit reports could be of interest to corporate IT forensic personnel, law enforcement agencies, anyone in the legal community, and forensic criminal investigators. They are capable of processing large amounts of log file data and support several types of log file formats such as Blue Coat and IronPort. The new reports are as follows:
- Search Terms Audit Detail – The report shows search terms that users entered on popular search engine sites such as Google. It includes an option to show “prefetched” search results that were performed as the user was typing. These results are referred to as keystroke searches. This report can be used as a tool to aid in forensic investigations. It also indicates the number of search terms entered and can give the details of a user’s keystrokes.
- Denied Detail – The report shows the specific URLs to which users were denied access. The data is broken out by user. Each Web page attempt is displayed with its corresponding category. Denied attempts for a Web page can signify that the user may not be authorized to receive the page, the page may not have been found by the Web server, or the page may have been blocked for access. If you have Web filtering enabled, this report can verify that it is working and is a very useful supplementary tool for individual user audits.
- Legal Liability Detail – The report shows the specific URLs of Legal Liability Web activity by user, that is, visits to only the Anonymous/Public Proxy, Cults, Drugs, Gambling, Hate and Crime, Malware, and Pornography categories that pose a legal liability risk. By reporting on only these categories, smaller, more focused reports are available to facilitate analyses, investigations, and audits related to legal liability issues.
To see the full release notes for your product, visit the Support Forum. You can download the latest release by going to the Administration – Product Update screen in your Cyfin or CyBlock product.
CEO Dennis McCabe spends a few minutes with CEOCFO Magazine
“We focus on both the security and forensic features that provide not just an IT solution but a company-wide solution.” Wavecrest Computing CEO Dennis McCabe spends a few minutes with CEOCFO Magazine
A Recognized Leader in Web Security Solutions, Wavecrest Computing Focuses on Maximizing the Benefits of Utilizing the Internet for Greater ROI and Provides Corporations with Essential Tools to Enforce Internet Use Policies and Protection.
Analyze Your Encrypted Traffic With CyBlock SSL Inspection

In huge numbers, more and more organizations, particularly e-businesses, are using Web-enabled applications that involve the use of personal, private, and sensitive data. Banking, online shopping, and credit card transactions are good examples, but by no means the only ones. SSL encryption is being increasingly used to protect the confidentiality of this business and personal data on the Web. Surveys show 25%-35% of enterprise traffic is SSL-encrypted, and the number can be as high as 70% in specific industries. SSL encryption is the most cost-effective way of protecting the privacy of this traffic.
While SSL encryption solves many privacy-protection problems, it can allow traffic that poses security threats–both inbound and outbound–to pass through security protection measures uninspected and unchecked.
Inbound Problem. SSL encryption creates security blind spots in incoming traffic. The traditional security infrastructure that protects an organization is blind to the threats in inbound SSL traffic and provides an easy vehicle for criminals and hackers to hide their cyber attacks.
Outbound Problem. In addition to the risks of incoming threats hiding over SSL channels bypassing security protections, outbound enterprise traffic is now a growing problem. This is becoming quite a “hot button” for security applications (e.g., content filtering applications) that tackle data loss prevention (DLP), compliance reporting, and lawful intercept. In the past these solutions could see what was outgoing, but now they are suddenly “in the dark” when it comes to the data transferred over SSL.
From a security standpoint, most organizations already deploy an array of network and security appliances and programs to protect their enterprise, enforce internal corporate acceptable use policies, and satisfy external government regulation. Unfortunately, in many instances, they can only inspect plaintext traffic and are unable to inspect HTTPS communications for attack signatures. This makes it difficult or impossible for network administrators to enforce corporate acceptable use policies or ensure threats, such as viruses, spam, and malware, are stopped before they reach individual users.
In addition, without the ability to examine the contents of HTTPS communications, network administrators leave open the possibility for information to be accidentally leaked out of the enterprise or worse, stolen. Regulatory compliance requirements, including identifying accidental or intentional leakage of confidential information, are also virtually impossible to meet because of HTTPS encryption.
CyBlock SSL Inspection gives network administrators the ability to monitor this SSL-encrypted traffic and to identify and respond to any undesirable content. The total HTTPS inspection process decrypts, analyzes, categorizes, and then re-encrypts the traffic. If necessary, specific standard and/or custom URL categories can be exempted from the inspection process; this is known as “tunneling.” In addition, full URL information in a number of Wavecrest audit reports is available to network administrators.
To learn more about how CyBlock SSL Inspection can protect your sensitive data, please see our SSL Inspection Tech Brief or contact Technical Support at (321) 953-5351, Ext. 4 or support@wavecrest.net.
Source: Examining SSL-Encrypted Communications – Netronome
Enhanced Malware Protection
Wavecrest Computing is pleased to announce an enhancement that delivers a tenfold increase in CyBlock’s ability to protect computer networks from malware and Cyfin’s ability to identify increasing security threats. Here is some background information.
Malware is the scourge of the Internet. The term “malware” includes computer viruses, worms, Trojan horses, spyware, adware, and other malicious programs that can disrupt computer operations, gather sensitive information, or gain access to private computer systems. For Wavecrest’s purposes, malware also includes Web sites that support hacking. Most malware originates and is spread from particular Web sites. Unfortunately, many thousands of such sites exist today, and to make matters worse, the number is growing steadily every day at distressingly fast rates.
The malware problem is not new to Wavecrest. For a number of years, companies have been using CyBlock and Cyfin products to protect against and identify automated invasions of malicious scripts and software, and unauthorized access to their internal networks–the two major problems caused by malware. CyBlock provided protection–under customer control–by blocking and reporting on employees’ attempts to visit sites in 3 of more than 70 URL List categories: Hacking, Phishing/Fraud, and Spyware/Malicious.
While this methodology was effective, it was not perfect. The difficulty lay in keeping the URL List up to date in the face of the relentless and rapid increase in the number of malware-spreading sites. This issue has been addressed with an enhancement that significantly improves the ability to keep the list current.
At the same time, three related categories, Hacking, Phishing/Fraud, and Spyware/Malicious, have been consolidated into one called Malware. This consolidation increases the ease of administration for customers.
This enhancement with its improved URL List is included in the latest release of CyBlock v.6.8.0 and Cyfin v.8.8.0. To realize its benefits as soon as possible, it is recommended that you upgrade your CyBlock or Cyfin product as soon as you can. Wavecrest will continue to update the enhanced list daily and make it available for download by customers. The download process remains unchanged.
You can schedule the list to be downloaded automatically every day, or you can download it manually at any time. In any case, as soon as it is downloaded, you will immediately begin to receive the added protection and see a significant reduction in the number of security threats to which you may be exposed.
To download the latest release, go to the Administration – Product Update screen in your CyBlock or Cyfin product. For additional assistance, please contact Technical Support at (321) 953-5351, Ext. 4 or support@wavecrest.net.
Cyfin Release 8.8.0 and CyBlock Release 6.8.0 Now Available
We are excited to announce the release of two major enhancements in the new version of Cyfin and CyBlock. The first major enhancement is the new SSL Inspection feature that allows our CyBlock products to decrypt, analyze, and fully inspect all HTTPS traffic. In order to defeat security threats facing companies today, SSL Inspection is essential. The second major enhancement is an innovative technique for protection against automated invasion of malicious scripts and software and/or unauthorized access to internal networks. Enhanced Malware Protection automates the process of identifying large numbers of new malware-spreading sites daily. To facilitate identifying and blocking malware traffic, three security threat categories have been consolidated into a new Malware category.
Other enhancements in this release include the rebranding of our products, new product icons displayed after installation, and new product Help. We also have a number of corrections in this release. The details of the enhancements include the following:
- Product Rebranding.The Wavecrest products have been rebranded as follows:
- The products offered are CyBlock and Cyfin (formerly Cyfin Reporter).
- Three deployment options are available for CyBlock:
- CyBlock Software (formerly CyBlock Proxy)
- CyBlock Appliance
- CyBlock ISA/TMG
- These changes are reflected on the Wavecrest Web site and the Forum. They will eventually transition to the products and associated documentation.
- SSL Inspection.This includes the following changes:
- Ability to view the full URL including path, embedded URLs, and parameters.
- Domain, path, and parameter matching.
- Ability to filter detailed HTTPS traffic by Web categories and Web content types and display blocking messages for both.
- Safe Search blocking (where applicable).
- Ability to view full URLs in the Real-Time Web Monitor.
- Ability to view full URLs in the following reports (where applicable), not just domains:
- Category Audit Detail
- Category Audit Summary
- Site Audit Detail
- User Audit Detail
- User Audit Summary
- A new SSL Inspection screen that allows you to select groups and/or IDs and standard and custom categories to be inspected. To access this screen, go to Advanced Settings – Proxy Settings – SSL Inspection. For inspection to occur, you must select a group and/or an ID, and set a category to Inspected. The Financial category is set to Tunneled by default for privacy reasons, but this can be changed to Inspected.
Note: Before using SSL Inspection, the Wavecrest Certificate must be installed. Refer to the Wavecrest Certificate Installation Guide for instructions on how to install/distribute the certificate. For more information on this enhancement, see the SSL Inspection Tech Brief.
- Enhanced Malware Protection in URL List.This includes the following changes:
- Extensive malware site additions were made to the URL List. You will receive the enhanced protection when the list is downloaded manually or automatically.
- The Hacking, Phishing/Fraud, and Spyware/Malicious categories were consolidated into a new Malware category.
- Custom URL entries categorized as Hacking, Phishing/Fraud, and Spyware/Malicious are now categorized as Malware.
- The Hacking, Phishing/Fraud, and Spyware/Malicious categories were replaced by the new Malware category on appropriate screens and in all category drop-down boxes.
- For CyBlock, on the Block Web Categories screen, the Malware category is set to “Block” in the Default policy in new installations by default. In existing installations, previous settings will not change when the product is upgraded, that is, the Malware category will be set to the previous Spyware/Malicious category setting.
- The Malware category is displayed on the Help – Reporting – Check URL screen under URL Category Match when there is a category match.
- Scheduled reports now report on the Malware category if they were set up to report on the Hacking, Phishing/Fraud, and Spyware/Malicious categories.
- Product Icons. The Wavecrest product icon has been replaced with new CyBlock and Cyfin product icons on the Start menu and on the browser tab (favicon).
- Product Help. The QR pages in the product have been replaced by a new searchable Help system. The Help system has a similar TOC as the product manual, but also includes an Index and a Search box. If a search result indicates “Web site,” you can right-click the entry to open the page in a new tab or window. You can also print a displayed Help topic by clicking the Print button.
To see the full release notes for your product, visit the Support Forum. You can download the latest release by going to the Administration – Product Update screen in your Cyfin or CyBlock product.
For additional assistance, please contact us.
What employers need to know about online holiday shopping
It’s that time of year again. Christmas is coming, and it’s time to find the best deals and research the best products. And where does everyone go these days to find the deals and do their product research? You guessed it. The Internet. Should employers be concerned with this? Absolutely! Online shopping results in significant productivity losses, excessive bandwidth usage and serious threats to cybersecurity.
Lost productivity can mean big bucks for your company. A recent study by Comscore found that 50% of all online holiday purchases occur during working hours. For the companies in the study, the typical productivity loss during the short holiday season averages $15,000.
Adding insult to injury, the additional traffic will lead to network slowdowns due to significant increases in bandwidth usage. Just as they did in previous years, online retailers are now preparing bandwidth-hogging promotional videos to help sell their products. Remember last year? On Cyber Monday 2011, video views increased by 897 percent over the previous year. And now the number of views this coming Cyber Monday are expected to exceed last year’s. So, it is critical to prevent vital bandwidth from being consumed by non-productive Web-use.
Contributing to the danger, hackers and identity thieves are very aware of these online shopping patterns. They are fully prepared to deceive online holiday shoppers with very appealing schemes – “deals” that require them to click a link to special discount or filling in personal information before they can get the deal. These acts can lead to malware infection or pose significant risks to your organization’s network and sensitive data.
The peak period for all these holiday-related problems is coming soon. The Comscore study tells us that 80% of all annual online purchases occur between Nov 26th (CyBer Monday) and Dec 14th. So now is a good time to remind your employees of your organization’s Web-use policy and make sure you have the right protections in place.
Dennis McCabe, President of Wavecrest Computing, recommends that companies monitor and/or filter employee Web-use to better protect themselves from lost productivity, excessive bandwidth usage and security threats. His company is ready to help them do this. Easy to use and priced to fit any budget, Wavecrest products are tailored to address all aspects of Web-use management reliably and cost-effectively.
About Wavecrest
Since 1996, Wavecrest Computing has developed, marketed, and supported a spectrum of innovative Internet usage monitoring, analysis, filtering, and reporting solutions. Their products help all types of organizations manage employees’ online activities, ensure compliance with acceptable use policies, preclude legal liability and prevent bandwidth abuse. Founded 15 years ago, their client base has grown to more than 3,000 organizations, including many prominent Fortune 500 companies and high-profile government agencies.
Cyfin Release 8.7.2 and CyBlock Release 6.7.2 Now Available
Upgrade today with the latest release of Cyfin and CyBlock. In this release, you will find new user guides, significant changes to the Dashboard charts, new pages to display errors, screen communication with the ISA plug-in as well as several corrections. The list of enhancements for CyBlock Proxy, CyBlock ISA, CyBlock Appliance, Cyfin Reporter, and Cyfin Proxy includes the following:
- User Guides. The user guides were enhanced to add a hyperlinked table of contents and additional hyperlinks in the chapters for ease of navigation when reading as electronic documents. The chapter and section headings, notes, cautions, and important information are color-coded for improved readability. With the improved layout, the user guides can be easily printed double-sided if you prefer to read in hard copy.
- Dashboard Charts. The charts and screens were modified to remove the need for Adobe Flash Player, add the ability to zoom in the chart, add a legend to toggle options on and off, and update other sections of the screens.
- Import From Active Directory. After creating or modifying an Active Directory configuration, you can now click an import link on the Configuration Completed screen. You will be directed to the Import – Active Directory – Manual screen to import groups and IDs.
- Error Pages. Error pages were added to display more detailed error information and allow information to be sent via e-mail to the administrator if the administrator e-mail is set up. The administrator can then submit the error and additional information to Wavecrest Technical Support.
- New Job Queue Section. For CyBlock, a Job Queue section was added to the Block Web Categories and Block Web Content screens to inform the user that jobs are running in the queue. If jobs are in the queue, this new section is displayed when the page is accessed or after submitting changes. The page is refreshed when the Job Queue is empty.
- Speed Up ISA Communication. The communication between the ISA plug-in and the CyBlock service was enhanced so that on the Edit URLs screen, only custom categories are loaded and not the entire URL List decreasing the load time. In addition, messages are now queued.
- Add Screen Communication for ISA.Changes were made to indicate that the ISA plug-in is communicating with specific screens while the communication messages are being queued. Messages will be displayed on the following screens:
- Login – Results
- Administration – System Information – Filter Status
- Advanced Settings – Filter Settings – Block Web Categories
- Advanced Settings – Filter Settings – Block Web Content
To see the full release notes for your product, visit the Support Forum. You can download the latest release by going to the Administration – Product Update screen in your Cyfin or CyBlock product.
For additional assistance, please contact us.
Coaching Now Available for CyBlock
Since 1996, Wavecrest has been creating solutions that help customers implement and enforce their Internet Usage policies. As the Internet landscape changes, some websites that were once categorized as unproductive are not so clear these days, causing current Acceptable Use Policies (AUP) to impede necessary productivity as organizations struggle to keep up with the ever-changing Internet. As part of Wavecrest’s mission to constantly improve, the coaching feature has recently been added to CyBlock Proxy v6.7 and CyBlock ISA / TMG v6.7 to alleviate this growing concern.
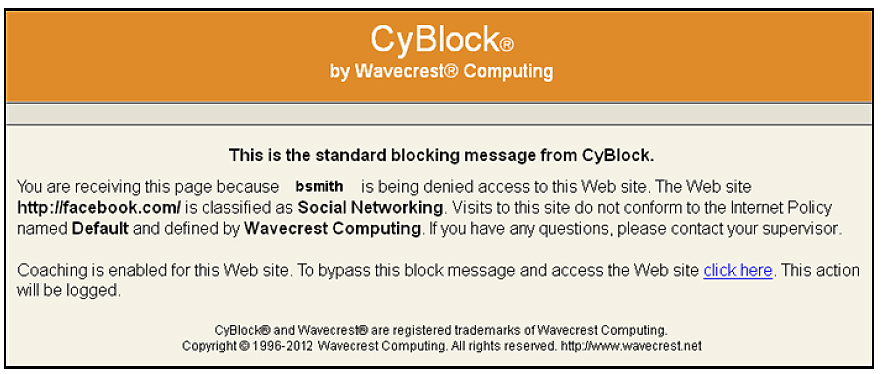
Customize this Message to Reflect Company AUP
This optional-use, customer-configurable, policy support feature allows authenticated / authorized users to override CyBlock’s blocking function while allowing them to proceed to the site they have requested. Coaching can be enabled on categories that have been set to “block”, and policies are customizable based on time of day, user name or group. The coaching feature provides customers with more flexibility and control while continuing to support their company policies through custom block messages.
For more information using CyBlock’s coaching function and creating your own custom blocking message, check out our easy-to-follow instructions on our latest Tech Tip: Create a Custom Blocking Message While Coaching.
Managing Bandwidth to Cut Unnecessary Costs

Inappropriate Web use resulting in excessive bandwidth consumption is often the primary culprit behind network issues. Typically, the worst offenders are social networking, video and music streaming, gaming sites, and browser-based file sharing. These are all widely accepted applications for use on corporate networks but the majority of them are often operating unchecked, opening your entire network up to bandwidth hogs, productivity-draining activity, and security risks.
There are multiple policies you can implement to monitor your bandwidth, so which one is right for your business? Pay attention to patterns: How much of your company’s bandwidth is being consumed by non-productive Web use? Who were the top users of bandwidth on your company’s network? Both questions seem easy enough to answer, but this data is oftentimes scattered around your network, especially if you have multiple data centers. Without easy access to these insights, many companies are simply unaware of possible lost revenue due to bandwidth congestion. Fortunately, Wavecrest Computing’s CyBlock Proxy solution now offers bandwidth management in addition to the Web filtering and reporting tools favored by many.
From within our solution, you can easily create multiple ‘category-control’ or ‘group-control’ policies that can be activated when usage reaches specified thresholds of consumption. Typically, customers set these thresholds at points that reflect how closely they want actual consumption to approach total available bandwidth before imposing restrictions. Once a policy is activated, policy-specified traffic is throttled one or more degrees of restriction on lower priority Web applications, allowing business-critical applications (VoIP, CRM, etc) to continue operating as needed.
While most other solutions base their throttling process on overall traffic volume rather than on the contents of the Internet packets, CyBlock Proxy breaks the traffic down into content categories and bases its controls on those categories rather than just volume. Alternatively, throttling can be imposed on selected users or groups, regardless of the content they’re seeking. The general concept is to synergistically combine your organization’s particular Internet and bandwidth usage policies with CyBlock Proxy’s customizable bandwidth throttling technology. Before you consider paying for more bandwidth, first leverage CyBlock Proxy’s built-in bandwidth management functionality (at no additional cost) by throttling the top non-critical bandwidth users. This feature has already provided businesses with the insight needed to most efficiently manage and utilize their Web traffic.