With the release of the new user interface, managing reports is easier than ever before. The new UI streamlines the way reports are managed by displaying recently run reports and scheduled reports all in one location. It also consolidates scheduling a report with creating a report. The following highlights of the new features describe how to navigate through reporting.
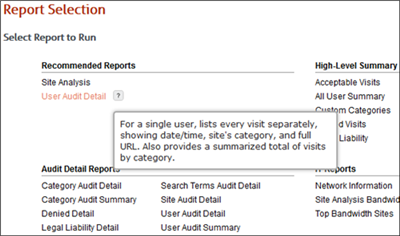
First, you need to select the type of report you want to create. On the Reports Selection page, the reports are grouped by similarity, and a Tooltip provides a short description of the report to help you determine which report to run. Click the name of the report that you want to run.
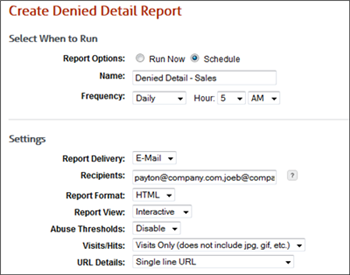
This takes you to the Create Report page where you can run the report at the present time (unscheduled). You can also schedule the report to run automatically at a specific time, that is, daily, weekly, or monthly at a specific hour, or set up the report to run manually as needed.
Report delivery options allow you to wait for the report, e-mail the report to multiple addresses that you specify, and save the report to a location. E-mailing reports to group recipients has been replaced with allowing you to easily specify each e-mail address to which you want to send the report. Recipients will also receive an e-mail should a report fail to run for any reason. Saving the report to a group directory has been replaced with allowing you to save to any directory. If the directory does not exist, it will be created.
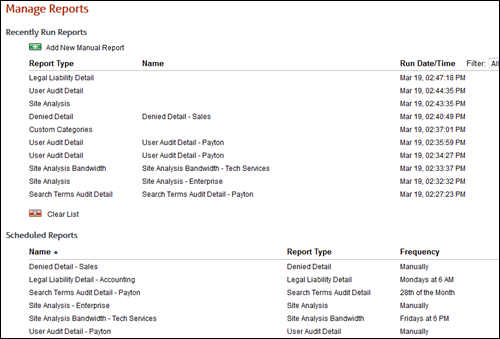
After you run or schedule your report, it will be displayed on the Manage Reports page.
The Recently Run Reports list shows all reports that were last run, that is, scheduled and unscheduled reports. The Scheduled Reports list shows reports that will run automatically at a specific time and those that will be run manually at a later time as needed.
Once you have run or scheduled reports, the Manage Reports page allows you to run, edit, duplicate, schedule, delete, and view these reports. You can also create new reports from this page.
For additional assistance, please contact Technical Support at (321) 953-5351, Ext. 4 or support@wavecrest.net.